New ADM 3.4. with Cersion 3.4 Comes with Fully Installed Linux Kernel 4.14
Provide improved stability and file system implementations. Allow maximum number of snapshots to any number under 256. Includes searchlights which enables searching for EZ Sync keywords and supports more languages.
Read More »
Life Saving Anti-Collision Software Integrated into First F-35s Seven Years Ahead of Schedule
FORT WORTH, Texas, July 24, 2019 /PRNewswire/ -- The F-35 Joint Program Office, U.S. Air Force and Lockheed Martin (NYSE: LMT) have started integrating the Automatic Ground Collision Avoidance System (Auto-GCAS) on to Air Force F-35As in the fleet. Leveraging a rapid, agile development, test and contracting approach, the joint government and industry team successfully fielded the life-saving...
Read More »
New VarIoT Technology Provides Real-time Product Data and Critical Temperature History
VarIoT Label size is 0.5” x 0.6” with custom options available. Displays product details, location of the temperature indicator, and product-specific temperature threshold. Features response temperature of 25°C to 71°C.
Read More »
New MRCGO Simplifies Procurement Process
Provide analysis tools for improved customer tracking and expediting of orders. Assist in strategic purchase planning through customer dashboard. Integrates with various third-party marketplaces and ERP systems.
Read More »
Inventory Management Services
This white paper provides an overview into the benefits, approaches and considerations for inventory management services.
Read More »
New IP PBX are Modular, Scalable and Adapts to Any Environment
Available with cloud based telephony and security features for leaner and faster framework. Helps to connect with clients, launch campaigns and funnel inbound calls to agents or to IVR. Available for enterprises with global operations and for VoIP service provide.
Read More »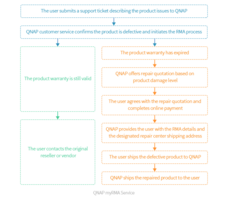
New myRMA Service Offers Extended Warranty Services for up to Five Years
Providing users suitable return material authorization services based on their product warranty status in the event of product damage. Users can contact QNAP by creating a support ticket on the Service Portal for their damaged product. Offers paid repair services if the product warranty has expired.
Read More »New Tektronix Video Monitoring Technology for Broadcast and Digital Media
Allows operators to correlate all alarms within a network in a single management platform. Enables rapid pinpointing of issues and resolution of faults. Suitable for linear broadcast and video headend monitoring applications.
Read More »
New PT6 App Available for Apple and Google Android Platforms
Optimizes the performance and availability of their PT6-powered aircraft. Enable users to select their aircraft model and manufacturer, so that information can be curated accordingy. app includes PT6 booklet content, excerpts from relevant service information letters and access to the P&W customer portal.
Read More »
New VisualSpreadsheet Software 5 Available for FlowCam Instruments and Desktop Systems
Provide the ability to compare data sets from multiple runs simultaneously. Capable to conduct time series analysis, allows users to monitor data and changes over time. Offers tools for data management and digitization.
Read More »
New hyperMILL 2019.2 CAD/CAM Software Enables More Secure Programming with Reduced Process Time
Features include high-precision 3D finishing, 5-axis tangent machining, high-performance turning, and CAD-for-CAM technologies. Utilities streamline CAM programming and provide tested and proven methodologies. Multiple faces can be joined into one face with controlled ISO orientation.
Read More »
Optimize Your Workforce with Weavix™ by PK Industrial
The Weavix™ platform takes productivity, quality, and visibility to a new level by providing better communication and real-time KPIs. Check out the video to learn more!
Read More »



